Smuggled in plain sight: SVG attacks, malware evasion, and the rise of SmuggleShield

Recently, Offensive Security Manager Dhiraj Mishra's research paper, The Art of Malware Smuggling (Unmasking SVG-Based Attack Techniques), and an open-source tool he developed over a weekend, SmuggleShield, were accepted at two major cybersecurity conferences: Insomni’hack (Switzerland) and Black Hat Asia (Singapore).
The research introduces “SVG Smuggling” — a technique for embedding malicious payloads inside SVG files that can bypass traditional network controls in enterprise environments. Since its disclosure, the method has reportedly been adopted in real-world attack campaigns.
At Insomni’hack, he presented a deep-dive technical analysis of SVG smuggling — its origin, mechanics, and implications — to an audience of over 250 cybersecurity professionals in Lausanne, Switzerland.

Breaking down SVG smuggling: Key takeaways from Insomni’hack
The research explores the evolution of HTML smuggling techniques with a specific focus on SVG-based attacks. This research is particularly important as it reveals sophisticated methods attackers use to bypass security controls and deliver malicious payloads.
What is HTML smuggling?
HTML smuggling is an evasive malware delivery technique that leverages legitimate HTML5 and JavaScript features to deploy malware, Remote Access Trojans (RATs), and other malicious payloads. This approach is particularly effective because it constructs the malicious payload directly within the victim’s browser, allowing it to bypass network security controls like proxies and firewalls.
Why this technique works:
- The attacker sends encoded HTML/JavaScript to the target
- This content passes through security controls because it appears legitimate
- JavaScript executes in the browser to decode a payload and create a file
- The browser initiates a download with a specific filename

From HTML to SVG: The evolution of smuggling techniques
What makes this research significant is the progression from basic HTML smuggling to more sophisticated SVG-based techniques. SVG (Scalable Vector Graphics) files are widely supported in browsers, email clients, and document viewers, making them ideal containers for smuggling malicious payloads.
The evolution of this attack technique has followed a timeline:
- Pre-2020: SVGs primarily used for phishing lures with limited impact
- 2020: Rise of HTML smuggling with JavaScript blobs and generic filenames
- Early 2021: SVG files begin embedding Base64-encoded payloads
- Late 2021: SVGs start incorporating embedded script payloads
- Mid-2022: Multi-stage SVG chains emerge with higher impact
- 2023: The Named File Smuggling technique was introduced —a method I discovered.
- 2024: Advanced techniques blending SVG smuggling with other file types
Named File Smuggling: A game-changing discovery
The core innovation of his research is the Named File Smuggling technique, which gives attackers full control over the downloaded file’s name and extension — a significant advantage for social engineering.
The technical implementation involves JavaScript code that creates a Blob object with malicious data and explicitly sets the download attribute to control the filename and extension:
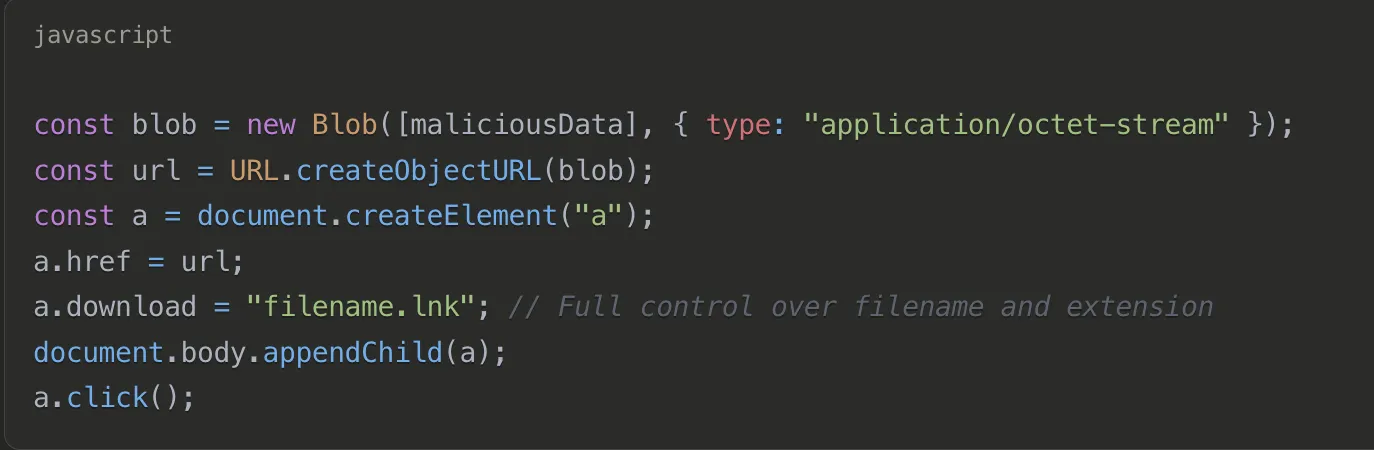
This technique has since been adopted by threat actors distributing malware such as Agent Tesla and XWorm.
In parallel, he began developing an open-source defensive tool, SmuggleShield, as a weekend project. This is a defensive tool that helps prevent file smuggling attacks. As of now, no enterprise vendors offer a robust solution that can prevent such attacks (HTML Smuggling). The tool is designed to provide effective prevention against such techniques.
SmuggleShield was showcased at Black Hat Asia 2025 in Singapore (3–4 April), drawing interest from around 100 attendees per session. The overall conference hosted over 1,200 participants. Notably, vendors like Cisco expressed interest in the tool’s methodology.

SmuggleShield: Open-source defence at Black Hat Arsenal
To counter these threats, he developed SmuggleShield, an open-source defensive tool designed to detect and prevent HTML and SVG smuggling attacks — a gap currently unaddressed by most enterprise solutions.
This tool:
Extracts six key features using machine learning, including:
- Base64 content length
- Blob usage patterns
- Download attribute manipulation
- Script density
- Encoding functions
- Binary manipulation techniques
Includes a continuous learning loop that tracks detection outcomes, refines future detection rules, and stores learned patterns locally for adaptive protection.
Here is a full user journey on how SmuggleShield works.
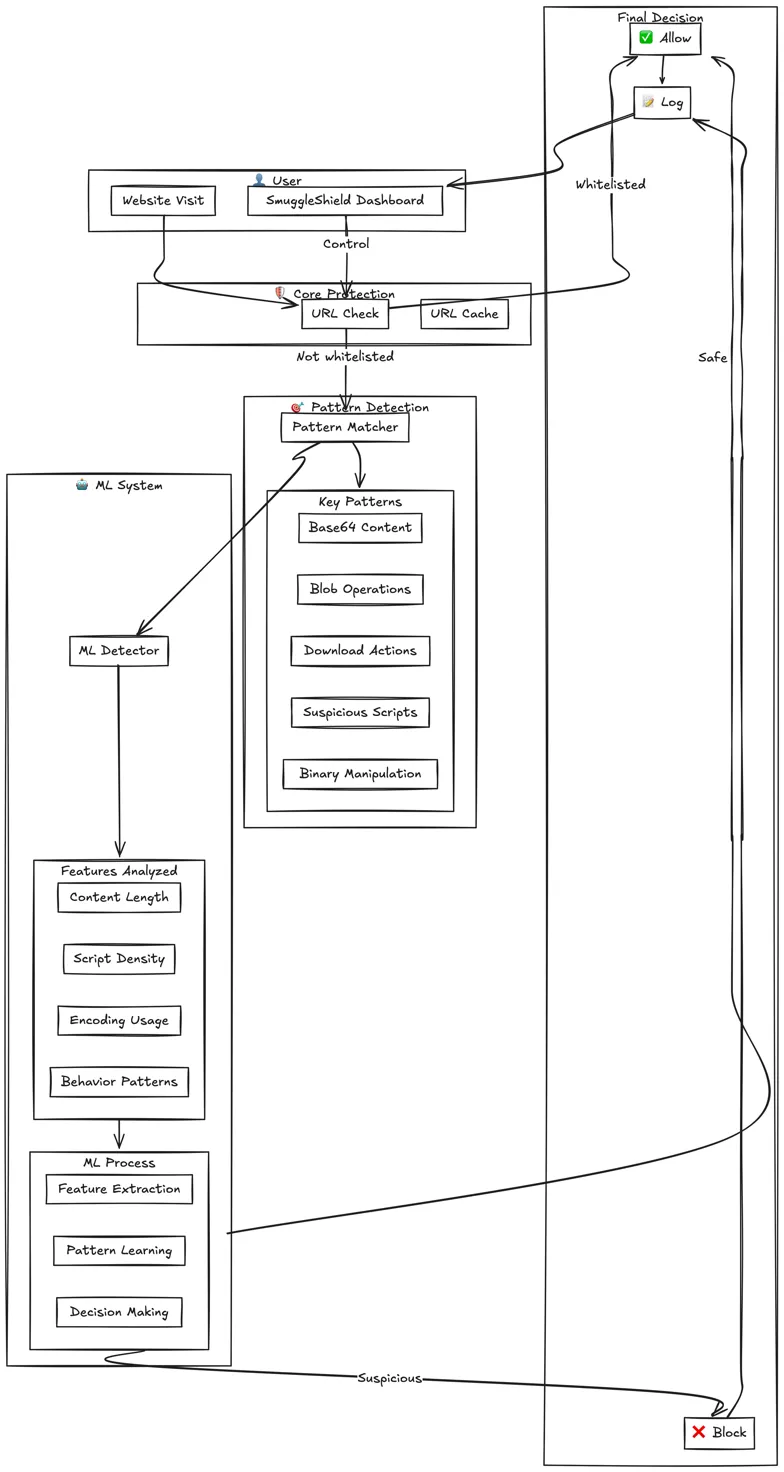
SmuggleShield has been effective in detecting and preventing various malware campaigns, including Shuckworm, Quakbot, DCRat, Pikabot, and AsyncRAT.
Why this research matters
This research highlights how attackers exploit trusted browser behaviour, not traditional vulnerabilities, to evade detection. SmuggleShield offers defenders a proactive, open-source solution in this ever-shifting threat landscape. SmuggleShield, as an open-source initiative, represents a significant step towards equipping defenders with practical, adaptive tools to pre-empt these advanced threats.
The open-source SmuggleShield project represents an important contribution to security tools that can help detect and prevent these sophisticated delivery techniques before malicious files can be downloaded to target systems.
References:
- https://github.com/RootUp/SmuggleShield
- https://github.com/surajpkhetani/AutoSmuggle
- https://cofense.com/blog/svg-files-abused-in-emerging-campaigns/
- https://insomnihack.ch/talks/the-art-of-malware-smuggling-unmasking-svg-based-attack-techniques/
- https://www.blackhat.com/asia-25/arsenal/schedule/#smuggleshield----basic-protection-against-html-smuggling-43154










.webp)


















%2520(1).png)
.webp)
.jpeg)



%2520(1).webp)
.webp)



.webp)
.webp)












.webp)





