漏洞賞金計劃條款
版本:
R25|04
最後更新日期:
June 27, 2024
此處可看到與漏洞賞金計劃參與者具體相關的條款和條件。 這些條款應與業務合作夥伴一般條款 (以下簡稱“一般條款”) 一併閱讀。 這些漏洞賞金計劃條款中使用的任何定義字詞均與《一般條款》中賦予的含義相同。
1. 介紹
1.1. 本條款適用於您自願參與的 Deriv 漏洞賞金計畫 (以下簡稱“計劃”)。該計劃旨在激勵參與者發現並報告 Deriv 軟體系統或網路中的漏洞或錯誤,並以此換取金錢獎勵。 當您向本公司報告與 Deriv 旗下任何網路服務相關的漏洞,或以其他方式參與本漏洞賞金計劃時,即表示您已閱讀、瞭解並同意接受本條款的全部內容。
1.2. 您承認本計劃不是競賽,而是實驗性且具有酌情性的獎勵計劃。
2. 範圍
2.1. 該計劃的範圍在計劃網頁上有詳細說明。 如果不確定某些內容是否屬於本計劃的範圍,請在進行任何測試之前,傳送電子郵件至 [email protected] 確認。
3. 合資格參加者
3.1. 如果是以下情況,則不能參加本計劃:
3.1.1. 您的雇主或工作的機構不允許您參與此類計劃;
3.1.2. 您現在或曾經是我們或我們任何集團公司的員工;
3.1.3. 您是我們或我們集團公司任何員工或前員工的直系親屬。
3.2. 如果我們知道或有理由懷疑您符合上述任何條件,我們保留取消您參與本計劃資格並收回任何賞金支付的權利。
4. 潛在獎勵
4.1. 我們保留決定提交的漏洞報告是否符合獎勵資格的權利。 我們保留決定提交的漏洞報告是否符合獎勵資格的權利。
4.2. 我們對賞金金額的所有決定均為最終決定。
4.3. 賞金金額範圍是基於受影響資料的分類和敏感度、漏洞利用的難易程度,以及如果安全團隊確認所報告的漏洞為有效安全問題,對客戶和品牌所帶來的整體風險。
5. 漏洞提交要求
5.1. 提交時需要遵循以下指南:
5.1.1. 請提供所報告漏洞的完整描述,包括其可利用性和影響。
5.1.2. 請提供完整的漏洞複現證據及逐步說明,內容應包括但不限於:
5.1.2.1. 視訊;
5.1.2.2. 螢幕擷取畫面;
5.1.2.3. 漏洞利用程式碼;
5.1.2.4. 流量日誌;
5.1.2.5. 網頁/API 要求和回應;
5.1.2.6. 任何測試帳戶的電子郵件地址或使用者 ID;和/或
5.1.2.7. 測試期間使用的 IP 位址.
5.2. 未能提供上述任何內容可能會延誤或阻礙賞金支付。
6. 敏感資料披露
6.1. 您同意未經我們書面同意,不得在本計劃之外討論已發現的漏洞 (即使是已解決的漏洞)。
6.2. 您承諾遵守 Deriv 的披露指南。 如果您認為自己發現了安全漏洞,請按照上述第 5 條規定的提交指南報告,並提供詳細的漏洞說明。
7. 執照
7.1. 您特此授予我們關於您提供的任何報告及回饋的免版稅、已全額支付、永久、不可撤銷、獨家、全球範圍內、可轉讓和可再授權的執照。 您同意我們對該報告和回饋擁有無限制的使用權。 我們保留不使用您提供的部分或全部內容的權利。 您放棄因報告中包含的任何資料或您向我們提供的有關產品和服務的任何回饋而獲得賠償的權利。
7.2. 您亦瞭解並承認,我們可能已開發或委託開發與您的提交內容相似或相同的資料,且您放棄因提交內容與上述資料的任何相似之處而產生的任何權利主張。 您瞭解,對於使用您的提交內容,您並不保證獲得任何賠償或署名認可。
7.3. 您聲明並保證,您提交的內容是您自己的作品,您沒有使用他人或實體擁有的資訊,並且根據此第 7 條款,您擁有授予我們執照的合法權利。
8. 您的義務
8.1. 除非您在參與時遵守所有適用的法律、規則和法規,否則不得參與本計劃。 您有責任了解並遵守您所在地區的法律,因為這些法律可能對您參與本計劃施加額外限制。
8.2. 您需自行承擔因參與本計劃而產生的任何稅務相關責任,具體取決於您的居住國和國籍。
8.3. 您的測試不得中斷或危及任何不屬於您的資料。
8.4. 您不得分享任何不當內容或資料。
8.5. 您不得侵犯任何第三方的權利,也不得從事任何侵犯他人隱私的活動。
8.6. 您不得參與任何對我們、本計畫或其他人有害的活動 (包括傳播病毒)。
1. 介紹
本指南旨在幫助有效且道德地推廣 Deriv。 透過遵循這些規則,可以與客戶建立信任,並體現 Deriv 的價值觀。 請仔細閱讀本指南。 如果您不遵循這些規則,可能不得不終止我們的夥伴關係。 如果有疑問或需要幫助,請與帳戶經理聯繫。
2. 品牌指導方針

在您的網站和您建立的任何行動應用程式上,請務必在 Deriv 標誌上方或前面展示字詞 "Powered by"。

清晰地溝通您與 Deriv 的關係。 使用如“與 Deriv 合作”和“與 Deriv 關聯”等字詞或介紹自己為 Deriv 聯盟會員。
不得使用 Deriv 的名稱和標誌建立群組或頻道。 在您的網站和平台上,您不能:
- 從 Deriv 網站複製整塊內容.
- 提及 Deriv 相關法規和監管者詳細資訊.
- 使用 Deriv 網站的 Deriv 員工詳細資料或圖像.
3. 建立線上形象

保持自己的風格。 避免使用與 Deriv 相同的配色方案或看起來或聽起來像 Deriv 的名稱。

作為 Deriv 合作夥伴,發展獨特的線上形象。 可以透過自己的網站或參與社交媒體平台實現。 例如,可以製作指導客戶如何開始使用 Deriv 或如何交易的影片。
確保社交媒體控制代碼和網站域名是唯一的。
切勿在使用者控制代碼中使用或包含公司名稱 Deriv。
4. 行銷和廣告標準
在 Facebook 或 Google 等平台透過付費廣告推廣 Deriv 之前,請向帳戶經理提交要求或傳送電子郵件至 [email protected]。 附上廣告文案、創意資料 (影片/圖像)、關鍵字和目標頁面。
在付費搜尋引擎活動中 (例如:Google,Bing),請勿對品牌關鍵字出價。
禁止關鍵字:deriv、deriv app、deriv broker、dtrader、deriv trading、deriv live account、deriv trader、deriv virtual account、bot trading deriv、deriv.com、www.deriv.com、deriv.com login、deriv mt5 trading、automated trading deriv、deriv register、deriv cfd trading、automated trading deriv。
- 使用聯盟儀表板上可用的行銷資料來推廣 Deriv。 如果要建立自己的行銷資料,請務必使用適當的風險警告。
- 請勿覆蓋、編輯或竄改 Deriv 提供的行銷資料。 任何內容不得模糊,字體應保持不變。
5. 促銷實踐
- 仔細規劃促銷市場活動,以確保貼文不會被視為垃圾郵件。
- 避免在社群媒體平台、群組、電子郵件或網站使用聯盟連結傳送垃圾郵件宣傳。
- 在 YouTube、Facebook、Instagram、X 和 Telegram 等合法社群媒體平台上適當地推廣 Deriv。
- 切勿在非法網站上使用彈出式廣告或促銷來宣傳聯盟連結。
6. 通訊和透明度

清楚定義正在推廣的服務。 明確顯示您支援的是交易平台,而不是賭場或快速致富計劃。 例如,不能將 Deriv 或其產品和服務表示為:
- 奢侈產品
- 輕鬆賺錢的平台
- 投資機會
- 任何保證收入或利潤的產品
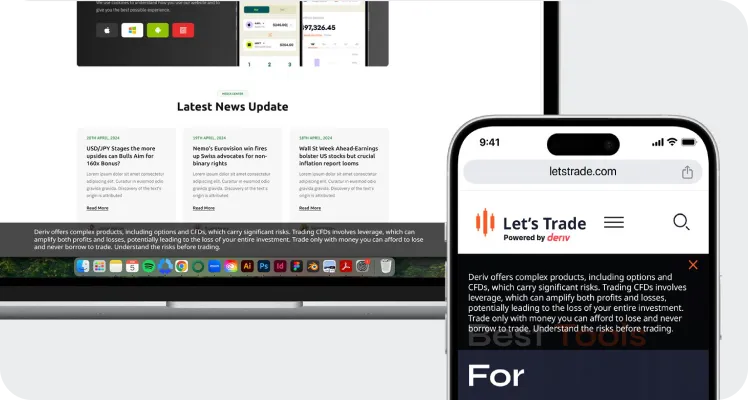
在顯著位置 (網站的標頭或頁尾,以可讀的字體和字型大小) 顯示以下風險免責聲明:
- “Deriv 提供包括期權和差價合約在內、且具有重大風險的複雜產品。 交易差價合約涉及槓桿,這可能會放大利潤與損失,從而可能導致全部投資虧損。 只用您能承擔的損失金額進行交易,切勿借錢交易。 在交易前了解風險。”
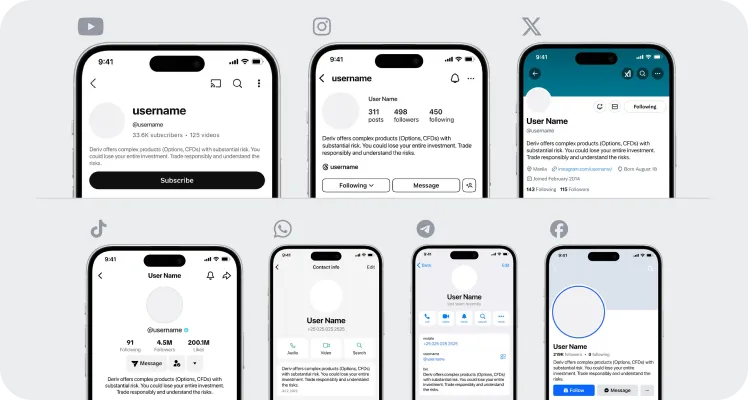
在社群媒體個人檔案中包含以下風險免責聲明,並將其作為橫幅圖像、個人簡介或置頂貼文發布:
- “Deriv 提供複雜的產品 (期權、差價合約),具有重大風險。 您可能會損失全部投資。 負責任地交易並了解風險。”
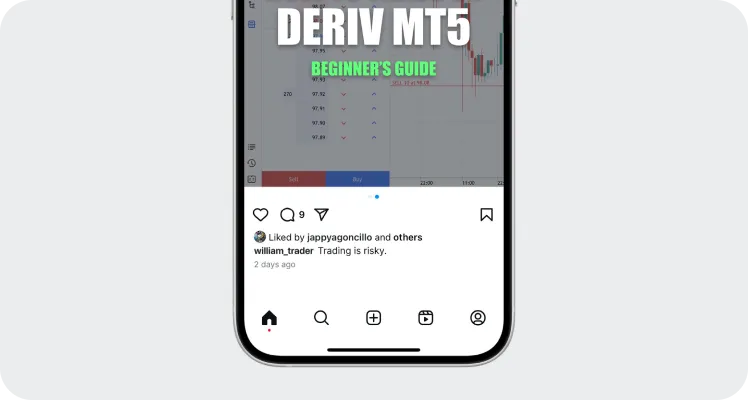
請務必在與 Deriv 相關的社群媒體貼文中加入下列風險免責聲明之一:
- “交易是有風險的.”
- 這不是投資建議。 交易涉及風險,並不適合所有人。
7. 尊重隱私
- 在任何活動中拍攝 Deriv 員工的照片或影片之前,請務必先獲得許可。
- 未經明確書面許可,切勿分享涉及 Deriv 員工的活動照片、影片或通話錄音。
8. 結論
遵循這些指導方針將幫助您作為 Deriv 聯盟會員建立良好的線上形象,增強客戶的信任並提升推廣效果。 我們的夥伴關係以相互尊重和遵守這些標準為基礎。 如有任何疑問或需要協助,請隨時與帳戶經理聯絡。